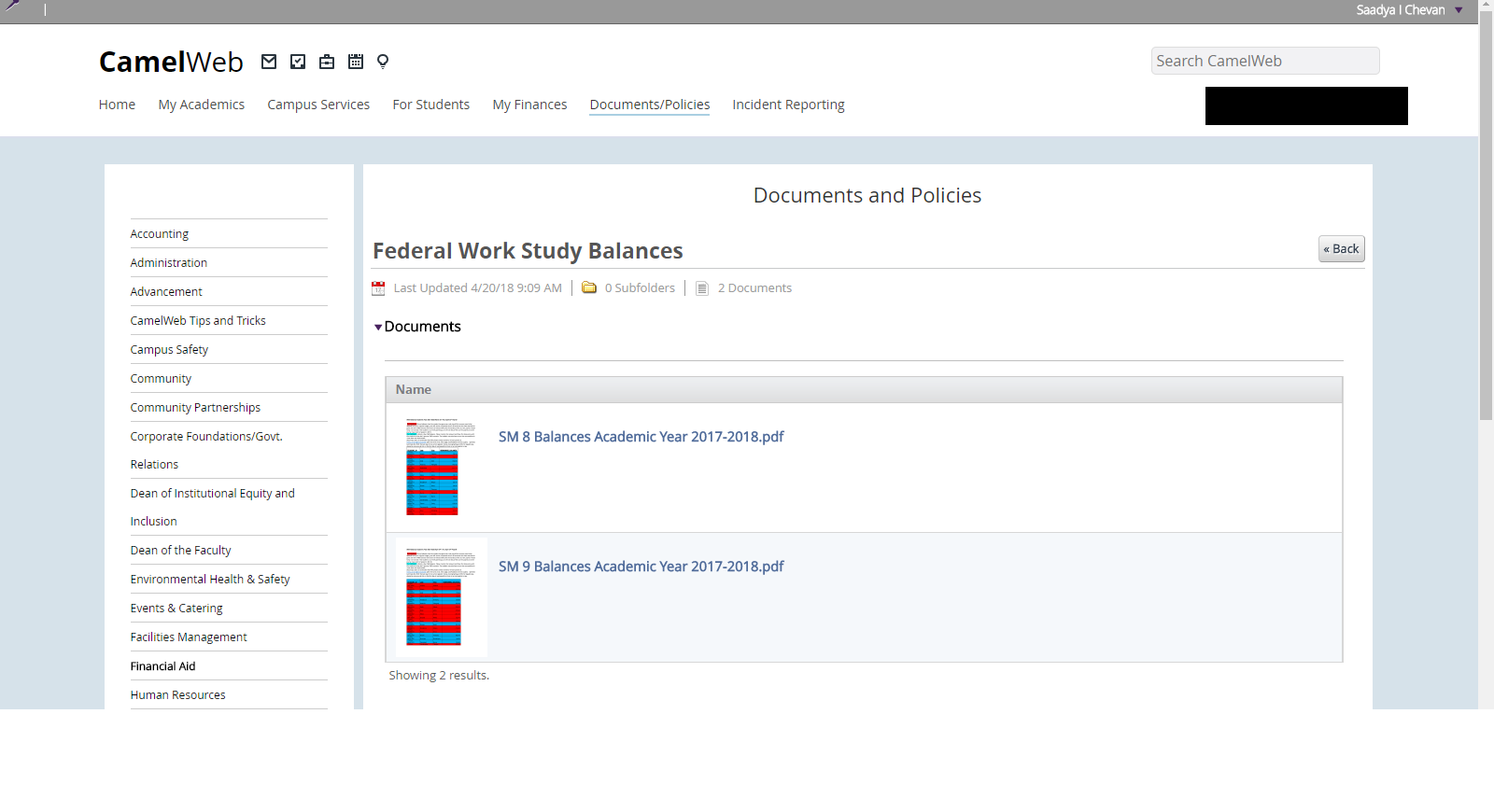
Last April, the College’s Financial Aid office uploaded and accidentally made visible to students, faculty, and staff two confidential documents containing federal work-study (FWS) balances of 107 students from two Spring 2018 pay-periods. The documents also reveal by implication that all of these students had applied for and received financial aid awards that included but may not have been limited to FWS funding during the Spring 2018 semester. They remained visible to students on CamelWeb until mid September when they were removed for reasons that remain unknown. The College’s information security staff, who are in charge of securing the College’s network and its confidential electronic data, were unaware of this flaw until the Voice disclosed that it had accessed these files on Oct. 8, which resulted in the immediate launch of an investigation by the College’s network administrators (Mr. Chevan also provided a recording and notes on an interview with Sean Martin, Director of Financial Aid, to the investigators). After this meeting, the subfolder they were stored on was removed. The Voice also disclosed its discovery to the Financial Aid Office later that same day. Lee Hisle, Vice-President for Information Services, has confirmed that the storage of these documents on CamelWeb made them accessible only to “students, faculty and staff with login credentials.” The Voice has run Google searches of some of the header material in these documents, which does not contain student information and did not find them in any of the results.
To understand the use of these documents, it is important to understand the logistics of colleges’ FWS programs. FWS is a fund paid to the College by the federal government based on its students’ eligibility for FWS funding and used to pay wages to FWS students. Whether students are eligible for FWS and how much money they can earn through the program is determined by the federal FAFSA application. Students funded through FWS have 75% of their wages paid through federal funds and 25% through the budgets of the offices that employ them with the exception of students employed to do community service work positions in New London and Norwich via Community Partnerships–a program with wages funded 100% by FWS.
However, when individual FWS students run out of funding for the semester, their supervisor(s) must decide whether to pay for the student’s continued employment fully from their own budget(s) or end their employment for the semester. Whether a student runs out of funding during the semester is dependent on the amount of the award and how many hours per week the student works in FWS positions. Because students run out of funding at different times, the documents serve as a channel for notifying supervisors about students who are low on funding or who have run out of funding and whose continued employment is being fully charged to their budgets.
The Voice spoke with four FWS students, three of whom requested anonymity, about their experiences budgeting their allotted awards to better understand how this system affects students. Some reported that their jobs gave them the amount of hours they wanted to work each week, or that they expected to earn the amount they had been awarded each year and not more. A student working at one of the on-campus coffee shops noted that because of the lower amount, they had been awarded in comparison to other students, they could not take extra shifts there.
Piper Oren ’20 who currently works FWS jobs at both Coffee Grounds and in the Office of Career Services opted to reduce hours worked at the career office this semester after taking a couple of extra shifts originally in anticipation of possibly studying away next semester. She stated that if she studied away next semester, she would be able to gain FWS employment, and therefore she wanted try to earn as much of her FWS award as possible this semester.
A third student said that their employment had been ended immediately prior to the spring finals period due to lack of FWS funds, but added that they felt this was convenient as it allowed them more time to study. The student stated that their supervisor, who worked in the Dean of the Faculty division, had once received an email requesting to end the student’s employment, but it was unclear if that email had been sent by the Financial Aid Office or from a higher level administrator in that the division.
The Voice also revealed and discussed the recent campus-wide availability of work study records with these students. The student who worked within the Dean of the Faculty Division, whose name appeared on both spreadsheets, expressed that they felt indifferent about the matter noted that they felt satisfied with their experiences as an FWS employee, and that this was not a serious issue compared to a hypothetical scenarios like the College underpaying FWS employees. The student who could not take extra shifts at a coffee shop also expressed that they were indifferent to the matter.
Two other students expressed varying degrees of dismay at the College’s handling of this. Neither of these students’ names appeared in either spreadsheet. Oren stated “I feel like it’s relatively sensitive information, but also it’s not necessarily somebody’s GPA or someone’s family income….It’s not the worst thing in the world to be leaked.”
The table below demonstrates the layout of data in the file:
| STUDENT ID | Last | First | REMAINING BALANCE |
| *TOTAL
00123456 |
Doe | Jane | -106.60 |
| *TOTAL
00123457 |
Doe | John | 89.10 |
Steven Mailloux and Tyler Campbell, administrators of the College’s network and the point people for data security incidents, said that Camel ID numbers are a public identifier used by the College, and therefore, the association of names with their corresponding ID numbers is not in and of itself confidential.
Campbell confirmed in an interview prior to the Voice’s disclosure about the files that the College would notify affected persons in the event of any data security incident. Jean Kilbride, Associate Vice President for Enterprise and Technical Systems, reiterated this statement after disclosure, noting that in any incident like this the College has to comply with the laws of the federal government, any of the states and other international jurisdictions that students are citizens or residents of that have passed laws relating to those students information.
The Voice contacted three alumni from the class of 2018, three current students and a former student who transferred to another college this semester. All of their names appeared on the lists. A screenshot of an email sent on Oct. 15, to one of these people appears above; a similar statement was also emailed to the Voice by Hisle on the same day. All of the current students confirmed that they had been notified. Of the alumni, two of the three had received the message, which was sent to their college email (alumni continue to have access to the college e-mail system). The transfer student reported they had not received any notification, but also observed that while they had not checked their college email since June, they believed they continued to have access to it. The Voice also spoke with several FWS students whose names were not on the list, all of whom stated they had not been notified suggesting that the college sent an email only to students who it identified as being on the lists.
Image courtesy of Saadya Chevan
The two alumni who received the message were both unclear on what data had been accessible. One of them had read the email prior to being contacted by the Voice while another, who had not, speculated that Hisle and his staff “probably don’t have another email and people would probably be annoyed if they received a call.”
There is some evidence that suggests that granting access to the documents to any member of the college is not allowed under FERPA, the Family Educational Rights and Privacy Act of 1974, which is the primary legislation governing protection of students’ data at US educational institutions. When asked to clarify if the event was a failure to comply with FERPA, in a follow-up email to the Voice, Hisle said “[The accidental access granted to the information] was not a data breach and did not violate state data breach laws, and notification was not required under FERPA.” However, the statement does not answer the question of whether this data is protected by FERPA, and according to the US Department of Education’s website, which sets regulations regarding FERPA, even if it were a FERPA regulated breach, direct notification of students would not be required.
The Code of Federal Regulations outlines the rules regarding FERPA protected data. It states that financial aid data is protected under the law, and individual students’ data may not be disclosed without each individual’s consent. However, there are exceptions that allow disclosure in connection with financial aid administration including to “enforce the terms and conditions of the aid,” which was the purpose of these documents. But according to LeRoy Rooker, currently a Senior Fellow at the American Association of Collegiate Registrars and Admissions Officers and former director of the US Department of Education’s Family Policy Compliance Office, which is in charge of FERPA implementation, an earlier clause in the code that requires that disclosures be “to other school officials, including teachers, within the agency or institution whom the agency or institution has determined to have legitimate educational interests” also applies to this section. This means that the College should only be giving students access to FERPA-protected information other than their own if they have a “legitimate educational interest” for accessing that data; in essence, if they were serving in an official capacity for the College (e.g. such an interest would apply to members of Honor Council who receive access to a student’s disciplinary records as part of a case).
In an interview prior to being informed of the Voice’s acquisition Sean Martin, director of Financial Aid, verified the documents’ existence and stated they were confidential: “We post a spreadsheet where employers can log in and see how much work study eligibility a student has for the [remainder of the semester]…. the only people that have access to it are staff members that we’ve granted access to, so it’s not like it’s visible to all.” Martin also noted that a work-study student employed by the office is not given any access to any other students’ information.
Prior to the Voice’s disclosure, Martin also said that he had never witnessed a breach or risky behavior regarding the Financial Aid Office or any other office’s security. He went into great detail about his office’s procedures regarding handling of physical data, but often deferred to Information Services on questions regarding security protocols for electronic data. He expressed confidence in his office’s security protocols saying “[Electronic data] is the scary part because that’s in the news right? That’s where I have a great deal of faith not only in Karen [Hoddinott] and how we do things here, but in our [Information Services] department and the safeguards that are in place, and how seriously they take data security….Given the type of info we have and the number of conversations we have with students and families: that’s the information that we take kind of most seriously. Forget about the tax returns and social security numbers: of course that’s important and we don’t email spreadsheets with sensitive data on it—we use FTPs with a lot of different vendors. It’s the conversational and via email: that’s the stuff we take very seriously as well. There’s those safeguards that [Information Services] has in place and then there’s the things that we have to guard ourselves against.”
After the disclosure, a reporter for the Voice made one attempt in person and two attempts via email to schedule a phone or in-person interview with Martin, who cited his and the reporter’s off-campus scheduling conflicts as the reason for declining all of them. When the reporter sent Martin a set of specific questions regarding how the financial aid office specifically handled these documents, he responded by saying that he felt that Hisle’s statement represented the views of all involved parties, including the Financial Aid Office. He also added the following statement along with a disclaimer stating that the short turn-around time requested by the reporter did not allow him enough time to give an adequate response: “As soon as we were aware of the access issue in April, we notified and worked with [Information Services] staff to remove the work-study balance posting and it was taken down within minutes of discovery. To my knowledge, that is the only instance of unauthorized individuals having access before or since. We have worked very closely and communicated clearly with our colleagues in [Information Services] in the past to make them aware of our data needs and to make sure that the appropriate safeguards are in place to both protect this data and allow access to authorized individuals…[sic] including with this work-study balance document. We look forward to continuing to do so in the future as well.”
In response to another follow-up question about how the financial aid office intends to revise its procedures regarding distributing information about FWS students’ balances, Martin stated “For the time being, we intend to communicate this information directly with individual supervisors/employers.”
The Voice approached employees in the Office of Religious and Spiritual Programs and Academic Resource Center (Mr. Chevan is employed by the ARC this semester as a tutor) who supervise FWS employees. None of them reported that they used the spreadsheet. Noel Garrett in the Academic Resource Center, who budgets but does not approve ARC student employees’ hours, reported that while he tracks his FWS employees’ funding throughout the semester, he does so based on the initial reporting of their award amounts. This process enables him to continue employing his FWS employees if they run out of FWS funding, he claimed “I know a lot of departments they don’t track it and all of a sudden the student is without work.” However, he declined to name any specific cases. Emphasizing that he didn’t feel the departments themselves were doing anything wrong Garrett observed “It’s unfortunate that once the [FWS] budget is gone [those departments] don’t have the budget to keep the student.”
The ability of Voice staff to access these documents via their student accounts certainly raises questions about the overall security of the Financial Aid Office and the entire College’s data. These files were stored on CamelWeb’s internal document storage system, but when a reporter initially asked Kilbride about storage on CamelWeb she claimed that files stored there were not confidential documents, but forms for the entire community or documents outlining policies. It was only after the reporter pointed out that the Voice had downloaded these files from this source that Kilbride acknowledged that she “taken by surprise” that something like this could happen at the College “this is not the way we [handle] any confidential information at all. In my knowledge you should not find it anywhere else, everything is usually a link to another system. I guess the only place I think we’d be vulnerable is in the ‘[CamelWeb] Documents/Policies.’”
An earlier statement made prior to the Voice’s disclosure about the overall status of FERPA and information security at the College, which was emailed to the Voice on Oct. 1, 2018, by Hisle, and written by Kilbride, Beth Labriola, the College’s Registrar, and Joe Lezon of Carousel Industries, who is the College’s Chief Information Security Officer, points to some of the things the College is doing well on the data security front. It notes that in Oct. 2017, the College “was recognized for the third year in a row, by the National Cyber Security Alliance as a NCSAM 2017 Champion for efforts in fostering a cybersecurity-aware campus.”
At various points the statement cites the College’s use of several third-party technologies and and contracting with third-party companies as evidence of excellent compliance. This includes constant monitoring and evaluation by the company Cygilant along with biannual assessments by an outside security firm, new required Duo Multifactor Authentication for faculty and staff and the company FireEye’s data security products.
The College’s Information Security team is currently developing a program to make data security a greater priority among people who do not work in Information Security or the greater Technical Support division as part of the Multi-Factor Authentication Policy approved on October 10, 2017. According to Campbell: “We’re in the process of identifying what we call data stewards…One person per department who is in charge of identifying the data that needs to be protected and also would hold the responsibility of auditing that department to make sure that the data is protected.” Kilbride, Mailloux and Campbell later acknowledged that incidents like this one were the exact reason they were creating this program.
All College employees handling Personally Identifiable Information, such as electronic student data covered under FERPA, are also required to take pass/fail online security training administered by the company SANS. If they fail to do so their network access is terminated.
Explaining previous security incidents the statement says: “the few incidents we’ve seen in recent years, generally ransomware, phishing or malware, occur primarily due to a lack of knowledge and training.” This and a previous statement from Mailloux suggest that the College has not recently been the subject of a breach.
Thus, despite the safeguards the College has in place to prevent these types of events from occurring, it remains unclear how exactly this inadvertent sharing took place. The most likely answer given the contrast between Martin’s initially expressed confidence in the Information Services department and Kilbride’s strong denials that CamelWeb is intended for sharing confidential documents is that there was a miscommunication between Financial Aid and Information Services about how these documents were being shared that likely would have been resolved had the data steward system been fully implemented prior to these documents sharing. However, based on the statements from both offices, no reasonable conclusion can be made about whether financial aid, Information Services, or both offices are primarily at fault for this event. •
CORRECTION: An earlier version of this article inaccurately stated that the investigation into the release of the work-study documents was conducted by Beazley, the College’s cyber security insurance firm. While this option was under consideration prior to the Information Security team being fully aware of the scope of the incident, they later determined that the data and exposure did not require a forensic investigation or statutory reporting.